
In the first part of this series, Secure Texting can be more than just securing messages, we discussed the key features (quick messaging, conversation threads, and required acknowledgment) of a secure messaging application that makes it a valuable texting tool for healthcare professionals. The first question healthcare organizations want a provider of a secure messaging application to answer,” Is the application HIPAA compliant?”. The first consideration should be the strength of an application’s data encryption and security. It is important to realize that being HIPAA and HITECH compliant does not guarantee that an application has a high level of security or that the PHI is not vulnerable to unauthorized access.Secure Texting Work with BYOD - Bring Your Own Device?A robust, secure texting application will have security features that work on both organizations-issued devices or in a “bring your own device” (BYOD) environment. These functions include strength of data encryption, storage of Protected Health Information (PHI) on user-owned devices/servers, central administration of users/devices, a consistent level of protection regardless of the device used (Apple, Android, PC), and portability of the application. It is also important to consider the total cost to the organization. This includes not only the cost of the application and services, but also the cost of certifying third party vendors for HIPAA compliance. It may be quite challenging to gather the security information, so it is important to see how easy or difficult the vendor makes it for you to compare their security features versus the cost of implementation.
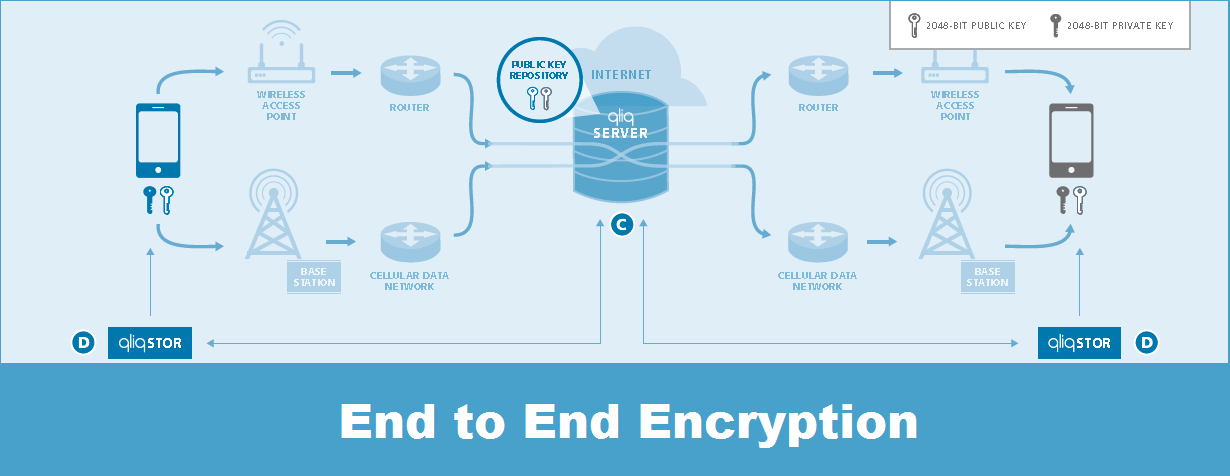
Because a majority of data breaches are due to lost or stolen devices with unencrypted data, the security of a secure messaging system must consist of end-to-end data encryption while in transit and at rest. It should be encoded by the sender, and only the receiver should be able to decode the message. As a way to prevent unauthorized access to the data, the application on the device must only be accessible through the use of a password or pin code, a distributed model (data storage across multiple devices) should be employed, and a central administrator should be able to lock or remotely wipe the device. Also, the central administrator should be able to automatically sync all devices when a member is added or removed, set group policies for password strength, idle lockout time, failure attempts, and message retention time. It is also important that PHI is not presented in the message alerts.

With increasing threat of data breaches that are estimated to cost healthcare organizations over $7 Billion, it is critical that all data is 100% under your control by being stored on your servers or in your cloud and on the end user’s device. In this way, you decide who will have access to your PHI and other sensitive data, when they will have access to it, and can ensure that a third party provider will not be able to access your data. Many vendors of secure messaging solutions use third party servers, such as Amazon, to store data which increases the vulnerability of your PHI to unauthorized access. They will tell you that a business associate agreement is not needed because the Federal Register, Vol. 75, No. 134, p. 40873 states that “…entities that act as mere conduits for the transportation of protected health information, but do not access the information other than on a random or infrequent basis are not business associates”. Are you comfortable with the fact that an Amazon employee or your vendor can access your PHI and other sensitive data at any time? At qliqSOFT, we believe that only the members of your organization should have access to your data. This is why we do not store PHI on our servers and only buffer the encrypted data. By doing this, we decrease the likelihood of unauthorized access or breaches. It is important to keep in mind that most data breaches occur after you stop using a service or by a rogue employee within your vendor’s organization. So, if your vendor does not have control or access to the data, a significant threat to your PHI is eliminated.
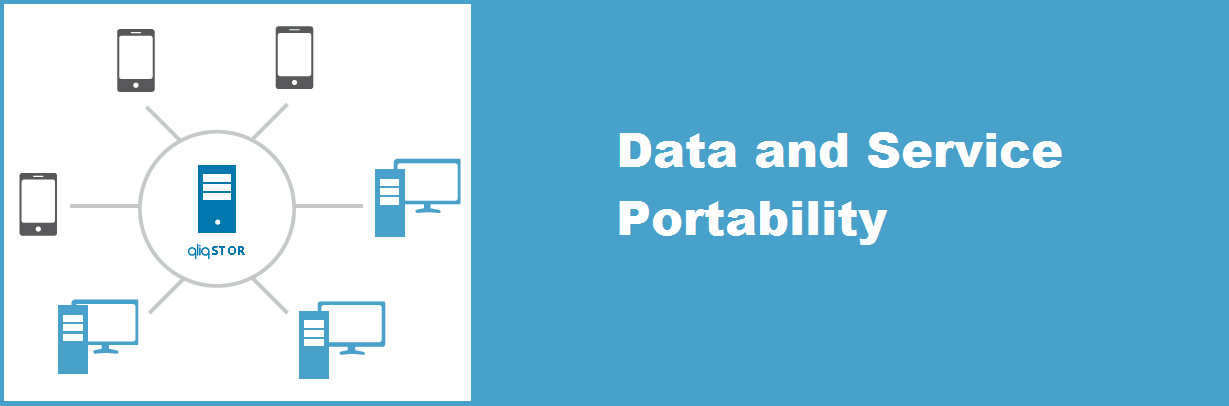
Data portability is an important feature for a secure messaging application. To have true data portability, the healthcare organization must have 100% control over the data. In this way, there are no issues with potential breaches after a switch is made to another vendor. Unfortunately with most vendors, your desire to change creates a potential security problem for you and them. Along with this, it is also important to consider the portability of the application. The application must be able to work with software ranging from Apple to Android to Windows to Mac and on any device (tablets, smartphones, laptops, and desktops) that a healthcare organization chooses to use. This flexibility allows the organization to grow organically and not get locked into particular products or pricing.
At QliqSOFT, we took care of message security, so you don’t have to. We use strong end-to-end data encryption that works across multiple platforms; we ensure that all PHI and other sensitive data is stored on your resources in a distributed model that is 100% under your control ensuring portability. Since only your organization can access the data, you do not have to worry about unauthorized access from a third-party vendor. In other words, we lower the risk of a potential breach while minimizing its impact. Each day we leverage our 18 plus years of experience in secure communications to develop further and improve the infrastructure we spent over 18 months in R&D developing. The best thing is that our secure messaging product, qliqConnect, is free and that we exceed the HIPAA and HITECH compliance standards saving you time and money on lengthy third-party validation procedures.
